Recently Microsoft released out of plan patches for the January updates` bugs. On the second Tuesday of January the company made the updates that caused many complaints from the customers. The problematic issues were with the Virtual machines (VMs), domain controllers (DCs) and VPN connections, etc. Users can download the updates from the Microsoft Update catalog. Some of the updates are available via the standard Windows Update system (as optional updates).
Patches KB5010794 (Windows 8.1, Windows Server 2012 R2) and KB5010797 (Windows Server 2012) are only available for manual download from the Microsoft catalog. With Windows Update, you can download the following updates:
Windows Server 2008 SP2: KB5010799
Windows 7 SP1: KB5010798
Windows 10 1507: KB5010789
Windows 10 1607, Windows Server 2016: KB5010790
Windows 10 1909, Windows Server, version 1909: KB5010792
Windows 10 20H1, Windows Server, version 20H1: KB5010793
Windows 10 20H2, Windows Server, version 20H2: KB5010793
Windows 10 21H1: KB5010793
Windows 10 21H2: KB5010793
Windows Server 2022: KB5010796
Windows 11 21H1 (original release): KB5010795
Microsoft`s January updates had several bugs
Before Microsoft released the out of plan patches for troubled updates administrators and users of Windows 10 and 11 complained of having problems after installing the January updates. Users complained that they started to have problems with L2TP VPN connections when working with the VPN client. When users attempted to connect to the the device it resulted in the following error:

In the event logs` journals it showed error code 789 indicating failed VPN connection. System administrators complained that latest updates also prevent them from connecting to the Cisco Meraki, SonicWall and WatchGuard firewalls.
Later the company took back the January cumulative update for Windows Server. Here the bugs messed up the work of the domain controller. It was forced to reboot. The problem touched Hyper-V and ReFS volumes as well. Hyper-V is a Microsoft technology that allows users to create virtual environments from multiple operating systems on a single physical server. In the January updates this virtualization tool somehow constantly crashed.
Resilient File System (ReFS) is a file system developed also by Microsoft that was created to overcome the limitations of NTFS (sometimes called ” The New Technology File System”). Users could not access its volumes due to the January update bugs.
Company released the said updates as part of the monthly set (Patch Tuesday). This month developers fixed six zero-day vulnerabilities and one critical. Updates for Windows Server have received the following IDs: KB5009555 (Windows Server 2022), KB5009557 (Windows Server 2019), and KB5009624 (Windows Server 2012 R2). These updates are currently not available in Windows Update.
What is RemotePotato0 vulnerability?
Another zero-day vulnerability Microsoft decided not to fix. The RemotePotato0 vulnerability allows for privilege escalation in all versions of the Windows operating system. It received an unofficial patch from 0patch. The vulnerability has not received its own CVE ID. In case of successful exploitation can lead to a complete compromise of the domain.
SentinelLabs specialist Antonio Kokomatsi first drew attention to the problem in April 2021. Exploiting the vulnerability, potential threat actors can get domain administrator rights by attacking the NTLM relay.
“RemotePotato0 allows a low-privileged attacker to run several special applications in any other user’s session. These applications can send an NTLM hash to an IP address that the attacker chooses. As a result, an attacker has the opportunity to forge his request to the domain and pose as an administrator. After that, the attacker can add himself to the administrators group,” 0patch founder Mitya Kolsek commented on the vulnerability in the company`s blog.
But the exploitation of the vulnerability can be possible only if an attacker somehow forces the person with administrative privileges to log in at the same time as them. Only this way the exploitation will be successful. The unofficial patch will be available until Microsoft releases the official one.
What is Microsoft Update Catalog and how to use it?
While there is nothing difficult with applying updates through Windows Update (you just simply have to run the download by yourself if it is not set to automatically do so) you may be confused by the term “Microsoft Update Catalog”. Microsoft Update Catalog is a Microsoft service that provides users with a repository or list of updates for all operating systems that Microsoft supports at the moment. The material ranges from hotfixes, Windows features, updated system files to device drivers.
Actually the thing is created for the use by enterprises and businesses but ordinary users can use it as well. You may need to use the service in case you look for a specific update for your computer. Broken/missing driver, as an example. But IT administrators in corporate systems ensure with the help of the repository that computers under their domain are given the correct system updates or the new updates won’t affect computers work in the domain during important hours. Whatever the case might be, before you go to this place know the general rules.
You can access the site from any browser and will see just a plain search bar at the right side of the site. Now remember don`t type any vague search queries like “Security update” or “Windows 10 update”. The search can present you with up to thousands entries. No, you have to be specific here. The right way to find the needed update will be like this: KB5005033. The KB stands for Knowledge Base and the number is different for each update.
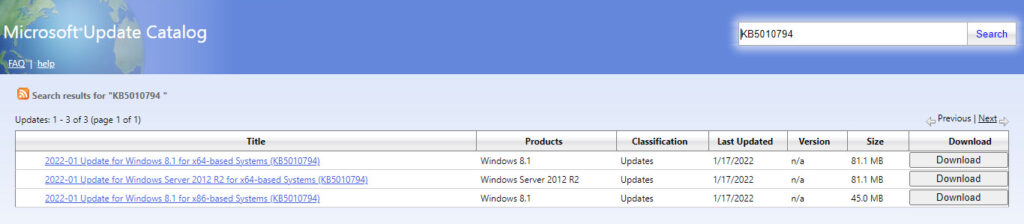
Just type it in and click the search button. You can also narrow down your search by adding more details about the query. For example, users may add x64 to show that they look for a 64-bit systems updates. Files with.msu extensions are simple installers. Those with .cab are archives for device drivers.
When you are presented with the result of the search click on the update to open up a separate window that will show you details of the chosen update. If it is the one you looked for, proceed to the download button.
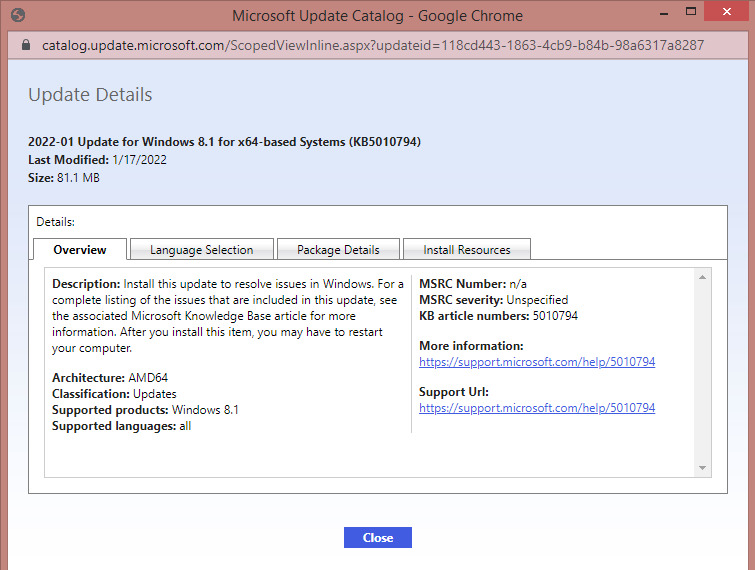
Keep in mind that some files have identical numbers. So make sure you checked the correct version and operating system.