The cybersecurity market is full of various products and services. All vendors ensure their customers that their product is superior and much better than one offered by rivals. However, the overall trend of making anti-malware software an all-in-one app. Following the wish to make the antivirus omnipotent, they pushed its resource consumption sky-high. Some examples of anti-malware software consume so much PC power that users call it bloatware. That’s why the choise of a reliable and convenient Trojan remover tool is essential.
Password managers, activity hours trackers, VPN services – all these things may be helpful. Still, not every user will use all of these services. However, purchasing a program means paying for all of its functions. But when paying for a thing, you would never use favorable for users? This factor and the chain of others lead the users to choose among the security tools that have the required minimum of functions without any excessive stuff.
I want to present Loaris Trojan Remover – the program that surely fits the program’s requirements. It has only the most needed functionality. So, what is Loaris Trojan Remover, and why do I think it will be ideal for PC protection?
Main Features of Free Trojan Remover
Loaris Trojan Remover is a lightweight anti-malware program capable of all essential functions needed to provide PC safety. It can perform various types of scans, reset browser settings and quarantine suspicious files. It additionally can fix the changes in system settings that malware usually brings into the attacked system.
Trojan Remover also features a range of settings that allow you to customize the critical functions of the application. We will have a look at them in the paragraphs below.
Security Features: How to Remove Trojan Virus
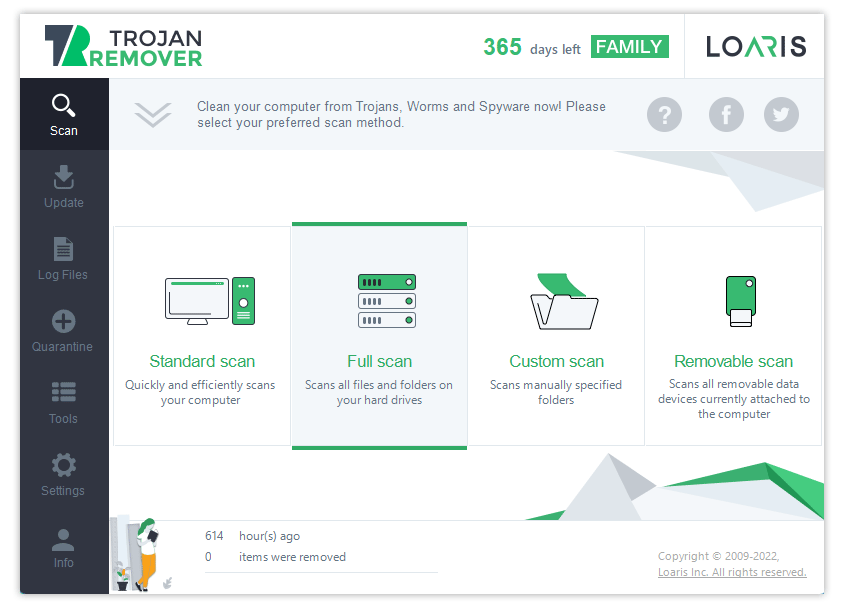
Loaris Trojan Remover offers four different scan types – Standard, Full, Custom, and Removable. All of them use the exact detection mechanisms but check other directories. There are three different ways Trojan Remover detects unwanted items on your computer – via databases, heuristic rules, and with the help of neural networks. Let’s have a quick look at how the Trojan removal process works.
- Database-backed detection is the alpha and omega of all anti-malware software. Even though the significant progress in other detection methods, this one remains the most popular among legacy AV programs. The share of total detections this method gives reaches 70-75%. It performs Trojan virus removal by comparing the hashes of the files you have on your disk with hashes of known malware. Match means that there is malware in your system.
- Detection with heuristic rules means the detailed observation of all actions performed by the applications. All malware does the same steps, this or another way. That does not depend on the file hash size, the form that the file is packed, and the language used to program it. Trojan checker heuristic system diligently checks applications’ routine calls and actions to detect possible hazards. Generally, heuristic rules are the basis for proactive protection features.
- Neural networks are the new word in anti-malware software development. While Trojan may circumvent both database-backed and heuristic detection algorithms, it can barely fool neural networks. Of course, they require proper training to function effectively. Obfuscation, repacking, downloaders – artificial intelligence will not miss it either. However, Trojan cleaner is still not ideal. They are not that great as a sole detection system, since it may have a lot of false-positive detections.
Advanced scanning systems
Trojan Remover applies these three techniques during all scans. All three types of scanning allow the users to provide maximal protection rates if applied combinedly. Here is how the removing Trojan virus process works:
- Standard Scan checks the default directories that malware uses to store its files. It pays special attention to the system drive – most viruses install themselves there. It takes about 5 minutes and is perfect for performing regular on-demand scans – just as prophylactics.
- A Full Scan checks all logical drives in the system – even the highest-level directories. Such diligence requires a lot of time and effort, so the program may take up to half an hour, depending on the number of files and CPU power. Nonetheless, this scan type is essential when you suspect malware presence and want to get rid of it.
- A Custom Scan is perfect for cases when you have an archive or a remote directory you are unsure about. Trojan Removal tool scans check only the opted directory, so it will take just seconds. The best way to prevent any malware from torrent downloads is to scan the downloaded files with that function, and you’re good to go.
- A Removable Scan is about scanning the portable drives. USB drives, removable HDDs, and SSDs are a very comfortable form of data storage and a perfect malware carrier. So to ensure that an unknown flash drive you’ve got somewhere is clean of viruses, launch this type of scan. It takes almost no time and can make your life much more accessible.
Wide Range of Trojan Removal Tool Functions
Besides a well-done protection mechanism, Loaris Trojan Remover can boast a wide range of side functionality that can help you fix the PC after the malware attack. For example, in contrast to some other anti-malware software, the best Trojan Remover allows you to reset your browser and networking settings manually without setting everything up after the malware removal.

- Reset Browser Settings makes it possible to wipe all the user-related data from the designated web browser without re-installing it. Such an option is needed after the activity of malware that involves your web browsers – primarily adware and browser hijackers. They can break a lot of important mechanisms that will make your experience much worse.
- Reset Windows HOSTS File is also a thing that must be used after a presence of a much more extensive range of malware types. Besides the threats above, HOSTS files are also changed by spyware, backdoors, and ransomware. That tiny text file configures your OS to determine the DNS for each site you visit. When it is adjusted for malicious purposes, you’d likely fail to open some websites or see phishing copies of those pages.
- Reset Windows Update Policies. Another thing that is a pretty famous victim of malicious interruption. Windows Updates frequently wipe the changes malware does to your registry and Group Policies. Without these alterations, malware loses a part or even the whole of its functionality. That’s why viruses may stop the updates by editing Windows Update Policies. Reverting them will bring the automatic patching back to your system. That is why it is vital to study the process and algorithms for removing Trojan viruses.
- Quarantine is a function that is almost obligatory for top-tier antivirus software but a pretty rare guest on antiviruses that are in the same price range as Trojan Remover. This function allows the user to keep the chosen files on the PC in the isolated memory area. Such an area prevents them from interacting with other data and the network. When you can designate in the settings, you may decide if you want to keep that file or wish to remove it. When the program is unsure about the detected file, it will automatically quarantine it.
Trojan Remover Download In A Few Steps
Try Trojan Remover’s free download process and set of functions by pressing the button below.
 Is a real RED light for the different kinds of spyware
Is a real RED light for the different kinds of spyware
First, you will download the mini-installer – which allows you to spend much less on traffic. Then, after the initial installation, you will get the other data – including some necessary detection signatures. After that, Trojan Remover will load the rest after pressing the Scan button.
Online Support
Loaris Trojan Remover offers 24/7 support if you have any questions or problems with our program. The support managers are glad to help you any time, in any language. To make the support work more accessible, you can give them technical information about your problem – of course, on their demand. They may ask you to provide two types of files: system information and scan logs.
- System information is generally required when specialists suspect the problem is on your side or the program cannot detect the malware. This log file has all the information about your hardware and software, including all installed programs. Having it, they will quickly figure out what goes wrong and give you recommendations.
- Scan logs are needed to see the outcomes of the scan you did. The information about the detected file name, its path in your file system, and the detection name may say a lot about the origins of this file. It is useful when you need to determine if you see a false detection or not.
Frequently Asked Questions
👉 How much does Trojan Remover cost?
👉 Does Trojan Virus Remover have proactive protection?
Loaris Trojan Remover is capable of running only on-demand scans. Such a decision is made to make the antivirus as lightweight as possible. Proactive protection features suppose the constant consumption of CPU and RAM while running in the background, which misses that conception.
👉 How good is the detection rate of Trojan Remover?
Loaris Trojan Remover can effectively beat most existing malware, and many will appear. Three detection mechanisms allow this app to keep a very high detection rate even offline – when there is no access to cloud databases.
👉 Is it obligatory to purchase Trojan Remover?
Trojan Remover has a full functionality trial. So you can run scans, remove threats and perform reset operations without paying a penny for the first 4-day trial. After trial period, malware removal and system repair will not be available. So to have the full functionality and be sure you are not infected, you are about to pay.