Exploit, or vulnerability exploitation, is a cybersecurity violation that allows hackers to perform a row of different actions beyond the design limitations. They have their own classification and can be spotted by the software vendor, a white hat hacker, or the crooks themselves. But how does it work? And how to prevent vulnerability exploitation? Let’s find out.
What is an exploit?
An exploit is a piece of software or code that takes advantage of a vulnerability or weakness in a system, application, or device to gain unauthorised access, control, or information. Exploits can be used to execute malicious code, bypass security measures, or cause system crashes or other unintended behaviours. They are often used by hackers, cybercriminals, and other malicious actors to carry out cyberattacks, such as stealing data, spreading malware, or taking control of a system.
It is important to keep the correct naming convention. The terms “exploit”, “exploitation” or “vulnerability” may sound synonymous to each other, but in fact, they’re not. “Exploit” may be referred to as both synonymous to exploitation and vulnerability. However, the last two terms differ. Exploitation is a process of using the vulnerability to conduct certain activities – most commonly illegal ones. Vulnerability, on the other hand, is the name for the exact security violation that allows it to exceed the normal limits. The exact functions that can be possessed by exploiting the vulnerability depend on its type.
Exploit types
There are a couple of the most significant types of vulnerability, the ones that often reach newsletter headlines. In fact, there are many more vulnerabilities that give no advantage to hackers or are too hard to exploit. They are generally getting patched in minor updates and are rarely mentioned even in patch notes.
Remote code execution vulnerabilities
Remote code execution (RCE) is a type of vulnerability in computer systems that allow attackers to execute code on a targeted system remotely, without needing physical access. That gives hackers an advantage of blind malware deployment: the only thing they need is to make the code run in the vulnerable environment. As there are numerous possibilities for that, hackers never disdain using RCE breaches. The impact of RCE attacks can be severe, as they allow attackers to bypass security measures and execute code with the same privileges as the targeted system or application.
Arbitrary code execution vulnerabilities
Arbitrary code execution (ACE) is a type of security vulnerability in computer systems where an attacker is able to execute any code they wish on a targeted system. This vulnerability can arise from flaws in software design, implementation, or configuration. The most common case is when the program has poor or no code control, and can execute code in different forms. Once an attacker gains access to a system, they commonly use ACE to install malware. That breach can take many different forms, depending on the vulnerability being exploited. For example, an attacker may use a buffer overflow exploit to overwrite critical memory locations and execute their own code. They may also use a SQL injection exploit to inject malicious code into a database. Then, it will be executed by the database engine.
Privileges escalation
Privilege escalation vulnerability is a type of security vulnerability that allows an attacker to gain higher-level privileges or access to a computer system or network than they are authorised to have. This vulnerability generally derives from poor privileges management. Commonly, the breach appears in apps that touch low-level system elements and in OS themselves. However, the main area of application for breaches that allow privilege escalation is granting malware (or an interim script) with higher execution privileges.
Buffer overflow
This type of exploit targets vulnerabilities in the memory allocation process of a program. The attacker sends more data than the program can handle, causing the extra data to overflow into adjacent memory locations. This can allow the attacker to execute malicious code or overwrite critical data. Some of the buffer overflow vulnerabilities have clear signs of being RCE or ACE breaches.
Zero-day vulnerabilities
Alpha and omega of sudden cyberattacks, the most unpredictable and threatening thing that can probably be faced. Zero-day exploits target previously unknown vulnerabilities in software or hardware. Because the vulnerability is unknown to the vendor, there is no patch or fix available. This makes zero-day exploits especially dangerous. There is only one way to protect your system against zero-days – zero-trust security solutions. Programs used to exploit zero-days are generally genuine and trusted – like MS Office or Photoshop. It means that regular AV engines will simply ignore the strange behaviour around the program.
Certain vulnerabilities are concentrated around a specific technology rather than programs. Some of them exist over a couple decades, and keep going today. The scale, diversity and aforementioned concentration allowed cybersecurity researchers to define them into separate categories. Their names are commonly used to describe the entire attack.
Cross-site scripting (XSS)
XSS exploits target web applications that allow user input to be displayed on a webpage. The attacker sends malicious code, typically in the form of a script, to the application, which is then executed by unsuspecting users who view the webpage. This can allow the attacker to steal cookies, capture keystrokes, or perform other malicious actions. Nowadays, XSS is commonly used to hijack crypto wallets and accounts on cryptocurrency exchanges.
Man-in-the-middle (MITM) vulnerabilities
MITM exploits allow intercepting and modifying communication between two parties. It allows the attacker to eavesdrop, steal information, or impersonate one of the parties. This type of exploit is commonly used in attacks on wireless networks or when communicating over unencrypted channels. Most often used and known examples of MITM touch unprotected Wi-Fi connections, or ones where hardware that provides the wireless connection is compromised.
SQL injection vulnerabilities
SQL injection exploits target web applications that use SQL databases. The attacker sends specially crafted SQL statements to the application, which can allow the attacker to bypass authentication and access sensitive data. Aside from actions related to accessing the DB without permission, SQL injection is often used for mischief. An infamous DROP DATABASE command is known even to people not familiar with hackery or database management. Fortunately, counteracting the SQL injection is relatively easy.
Examples of Attacks With Exploits
Almost every attack done nowadays uses at least one or a couple of exploits. Most commonly used one is a vulnerability in the MS Office macros handling mechanism. Due to the weak isolation of a sandbox they’re executed in, it is quite easy for attackers to circumvent the environment and start acting in a live system. However, most notorious attacks happen less often, and use breaches that further become worldwide-known.
WannaCry Ransomware
Possibly, one of the most known state-sponsored attacks ever. Conducted by the Lazarus group (North Korean government subsidiary cybercrime gang), it bore on the EternalBlue vulnerability. That breach is based on a vulnerable implementation of SMB protocol, present in all Windows versions before 2017. It can be classified as a buffer overflow attack, which allows the execution of arbitrary code. Hackers used it to deploy ransomware. Being based on a networking protocol, it allowed malware to spread through the local network pretty quickly. This exact breach was then used for the NotPetya ransomware attack in the year to follow.
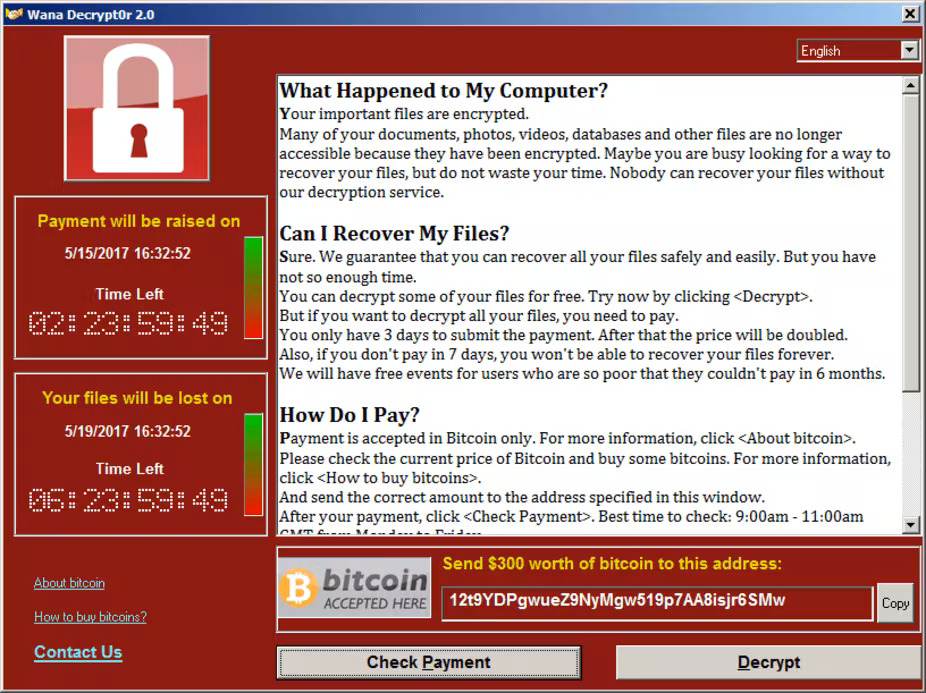
WannaCry ransomware note
Equifax Hack
In 2017, the credit reporting agency Equifax suffered a massive data breach that exposed the personal information of millions of people. It resulted in the theft of personal information, including names, Social Security numbers, birth dates, and addresses, of approximately 147 million individuals in the United States, Canada, and the United Kingdom.
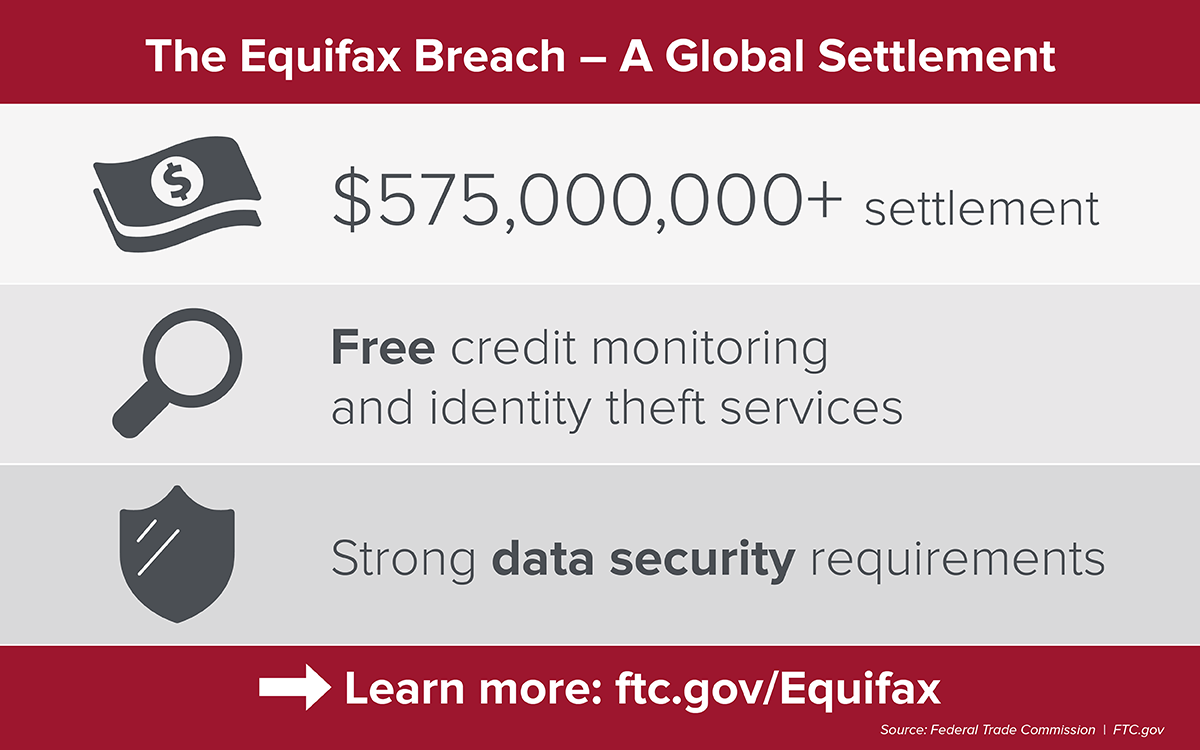
Summary on Equifax attack prepared by FTC
Hackers used a vulnerability in Apache Struts, a popular open-source web application framework. Specifically, the attackers exploited a flaw in the Struts framework that allowed them to execute arbitrary code on Equifax’s web servers. The attack began in mid-May 2017 and was not discovered until late July, when Equifax’s security team detected suspicious network traffic. However, it was later revealed that Equifax had failed to patch the vulnerability in a timely manner. That situation is conjoined with the fact that the company was notified of the vulnerability and a patch being available months before the attack.
SolarWinds Cyberattack
SolarWinds hack, discovered in December 2020, involved the exploitation of multiple vulnerabilities in the SolarWinds Orion network monitoring software. The attackers compromised the software supply chain and injected malicious code into the Orion software updates. Then, it was distributed to SolarWinds customers. Once the compromised software was installed on a system, the attackers were able to gain privileged access. They managed to steal sensitive information from the targeted organisations. The SolarWinds attack was highly sophisticated and involved multiple stages, including the use of custom-built malware, domain fronting techniques, and careful selection of targets.
How to be protected from exploits?
To protect against exploits, it is important to keep software and hardware up to date with the latest security patches and updates. Organisations should also implement strong access controls, such as multifactor authentication, to limit the risk of unauthorised access. Regular security testing and vulnerability assessments can also help identify and mitigate potential vulnerabilities before they can be exploited. Aside from testing and research, there are several pieces of advice that can work proactively for your good.
- Use a zero-trust security solution. As I have mentioned it already, the only way to be sure about your protection against zero-day exploits is giving no trust to programs at all. Zero-trust policy in its very essence supposes that all apps should be treated as potentially hazardous. Aside from zero-days, it will be pretty effective against more regular exploitation as well.
- Update software as often as possible. Another proactive approach towards minimising risk of vulnerability exploitation is installing all updates for your software. It will be an even better practice if you track recent cybersecurity news – that will help you to be aware of potential hazards within your software.
- Don’t interact with questionable files. Wherever you find them, it is a bad idea to make them run, even if you have anti-malware software running in your system. Email spam and cracked software were and remain one of the biggest sources of malware – thus it is at least reckless to run it. And hackers who operate this malware are eager to see if your system is vulnerable.
In summary, exploits are a serious threat to computer systems and networks, and can have significant consequences for organisations and individuals. Staying vigilant and taking proactive steps to protect against exploits is essential to maintaining the security and integrity of computer systems and data.