Reports about data leaks in large and not-so-large companies have become increasingly frequent lately. Data breaches and leaks refer to unauthorized access or disclosure of sensitive data, which can have severe consequences for the organization and those whose data is leaked. Next, we’ll break down what Data Leaks and Data Breaches are, how these terms differ, and what steps you should take to minimize the chances of Data Breaches.
What is a Data Breach?
Data breaches are the situations when an unauthorized party accesses, discloses or steals confidential or sensitive information. It can occur for various reasons, such as human error, system glitches, or cyberattacks. In addition, data breaches affect different types of information, including personally identifying information (PII), financial data, health records, or intellectual property.
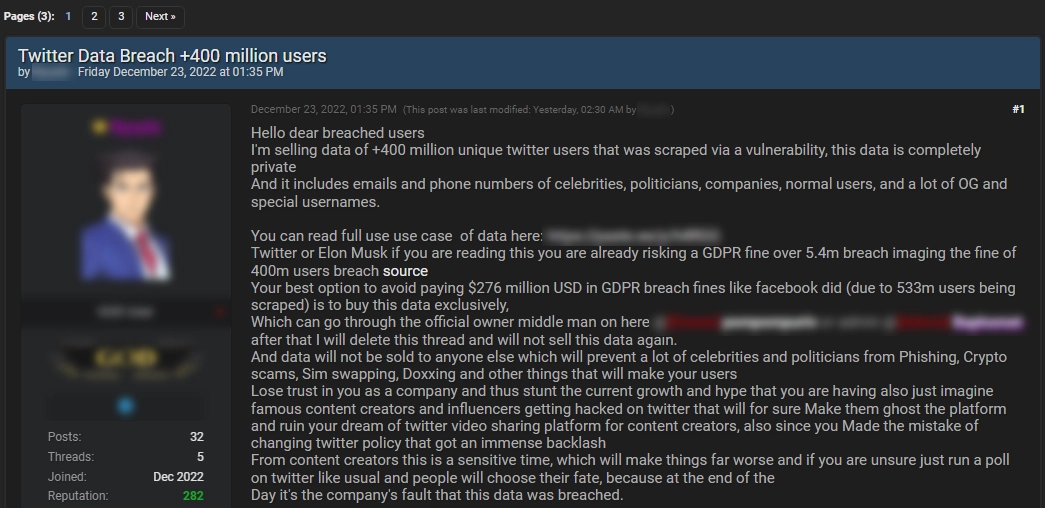
A post about selling leaked Twitter data on a hacker forum.
Hackers may use stolen data for malicious purposes, such as identity theft, financial fraud, or espionage. As a result, data breaches can have hurtful consequences for both individuals and organizations. For example, for individuals, the loss of personal information can lead to financial losses, reputation damage, and emotional distress. In turn, for organizations, data breaches can result in legal liabilities, loss of customer trust, and economic losses due to regulatory fines, remediation costs, and business interruption.
How Does a Data Breach Occur?
Data breaches can occur for many reasons, often involving exploiting vulnerabilities in an organization’s IT systems or human error. In addition, it can be caused by the following factors:
- Human error: This is one of the leading causes of data breaches. Employees or individuals may accidentally send sensitive information to the wrong person, leave a device unsecured, or fall victim to phishing attacks.
- Cyberattacks: These are intentional attacks by hackers who exploit system vulnerabilities to gain unauthorized access to sensitive data. Common cyberattacks include malware, ransomware, phishing, and social engineering.
- Insider threats: These are data breaches caused by individuals with authorized access to the system, such as employees or contractors, who intentionally or accidentally misuse the data. It can be due to dissatisfaction with the company, personal gain, or negligence.
- Physical theft or loss: Data breaches can also occur when physical devices, such as laptops or hard drives, are lost or stolen, and the data stored on them is not correctly encrypted or secured.
- Third-party breaches occur when a third-party vendor or supplier with access to a company’s data is compromised, exposing sensitive information.
What is a Data Leak?
A data leak, similar to a data breach, is a data security incident that occurs when sensitive or confidential information is disclosed to unauthorized individuals or entities. This can happen intentionally or unintentionally, but the result is the same: sensitive data ends up in the wrong hands. The main difference between a data breach and a data leak is that external factors, such as hacking or malware attacks, usually cause a breach. In contrast, a data leak is often the result of internal actions, such as human error or negligence. Moreover, data breaches typically involve the theft or compromise of large amounts of sensitive data. In contrast, data leaks often involve the accidental or deliberate disclosure of more minor data.
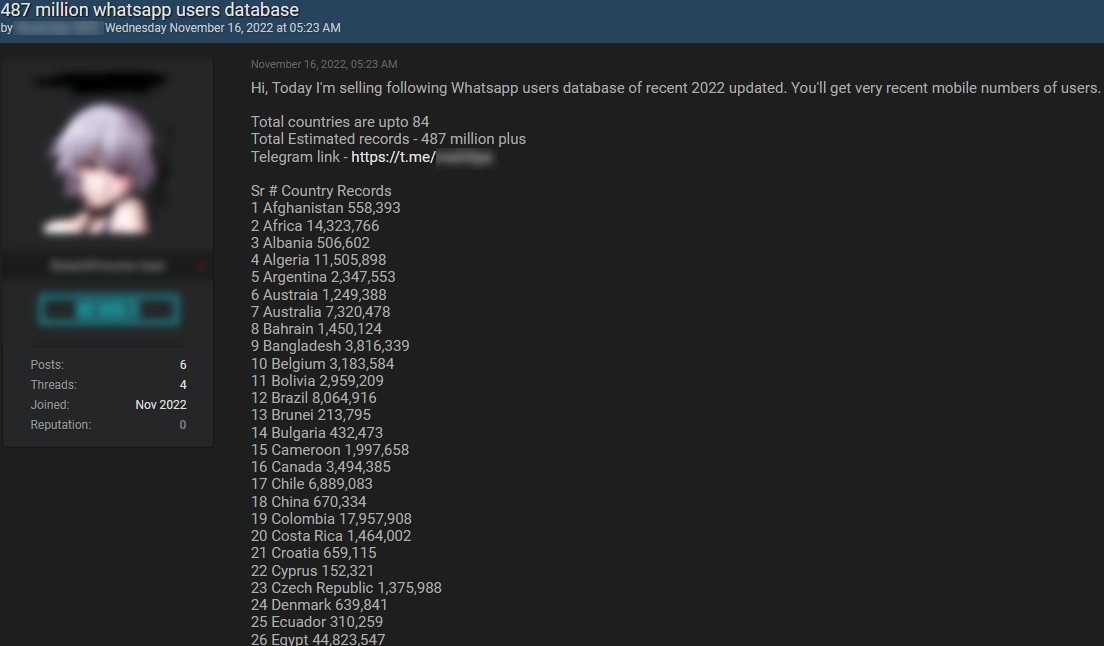
Another post about selling leaked Whatsapp data on a hacker forum.
Another key difference is the nature of the data involved. As we mentioned earlier, data breaches typically involve the theft or exposure of personally identifiable information, such as addresses, names, Social Security numbers, and financial information. Data leaks, on the other hand, can involve any type of sensitive information, including trade secrets, intellectual property, confidential business information, and internal communications. In terms of consequences, data breaches and data leaks can both have profound financial, legal, and reputational implications for businesses and individuals. However, data breaches are often seen as more severe because they involve intentional attacks by external actors and may result in more widespread damage.
Causes of Data Leaks
Data leaks can occur for various reasons, both intentional and unintentional. However, some common causes of data leaks are:
- Human Error: Human error is one of the most common causes of data leaks. Employees may accidentally send sensitive data to the wrong recipient, leave confidential documents unsecured, or fail to follow data security protocols.
- Phishing: Phishing attacks are among the most common methods cybercriminals use to steal data. They use emails, phone calls, or text messages to trick employees into revealing sensitive information, such as login credentials or financial information.
- Third-Party Vendors: Third-party vendors with access to a company’s network or data can also cause data leaks. They may have weak security protocols or follow different data security standards than the company.
- Physical Theft: Theft of laptops, mobile devices, or other storage media can also cause data leaks. Suppose these devices contain sensitive data and are not encrypted or password protected. In that case, anyone who gains access to them can retrieve the data.
- Misconfigured Cloud Services: Misconfigured cloud services can lead to data leaks, as they may expose data to unauthorized users or allow public access to sensitive information.
What is Worse? Data Breach or Data Leak?
Data breaches and data leaks are both severe security incidents that can result in sensitive data being exposed. However, while they share similarities, there are differences between them that can impact their severity. For example, the violation can be intentional or unintentional, and the attacker may be after financial gain, trade secrets, or personal information. On the other hand, a data leak occurs when sensitive information is unintentionally exposed to unauthorized parties. A data leak can happen in several ways, including through human error, system glitches, or misconfigured software. However, unlike a data breach, a data leak is typically accidental and not caused by malicious intent.
So, which one is worse? It depends on the specific circumstances. Both can harm an organization’s reputation and financial stability. However, a data breach can be more severe than a data leak. Data breaches can lead to heavy financial losses, lawsuits, and regulatory fines. In addition, the failure of sensitive data such as bank details, social security numbers, or medical records can also result in identity theft or other forms of fraud, causing long-lasting damage to affected individuals. Additionally, data breaches can lead to a loss of trust between the organization and its customers, resulting in reputational damage that can be challenging to overcome.
On the other hand, a data leak is still a serious incident. However, it may not result in as severe consequences as a data breach. For example, data leaks can still cause reputational damage, loss of customers, and regulatory fines. However, they are less likely to commit identity theft or financial fraud. In conclusion, data breaches and leaks are significant security incidents requiring immediate attention from the affected organization. The severity of each incident will depend on the specific circumstances.
How to Prevent Data Breaches
The best way to prevent these breaches is to be proactive. Here are some critical steps that businesses can take to minimize the risk of data breaches:
- Implement Strong Password Policies: Employees should use complex and regularly updated passwords. In addition, use two-factor authentication whenever possible.
- Train Employees: Employees should be trained to identify and avoid potential security threats like phishing attacks, social engineering, and malware. It’s essential to keep security awareness training up-to-date and ongoing.
- Limit Access to Sensitive Data: Grant access to those employees who require it for their job function. Limiting access to sensitive data can help reduce the risk of data breaches.
- Keep Software and Systems Up-to-Date: Regularly updating software and systems can help patch vulnerabilities and prevent cyberattacks. Failure to do so can leave an organization’s strategy open to attacks.
- Use Encryption: Encrypting sensitive data can add an extra layer of security. In a data breach, the stolen data will be unreadable to the attacker.
- Regularly Back Up Data: Regular data backups can ensure an organization can quickly recover from a data breach or other cyberattack.
- Perform Regular Security Audits: Security audits help identify potential vulnerabilities and threats. Therefore, it’s essential to review and improve security measures continually.
Organizations can reduce the likelihood and impact of data breaches by implementing these preventive measures. However, security measures are not foolproof, and developing a response plan is essential in the event of a breach.