Network Detection and Response (NDR) is a cybersecurity solution designed to identify, investigate, and respond to security incidents on a network. The conception of NDR appeared long ago, but software that corresponds to this definition is not that old. Let’s have a look what this software is needed for, how it works, and what its pros and cons are. And finally — is NDR a must-have solution?
What is Network Detection and Response?
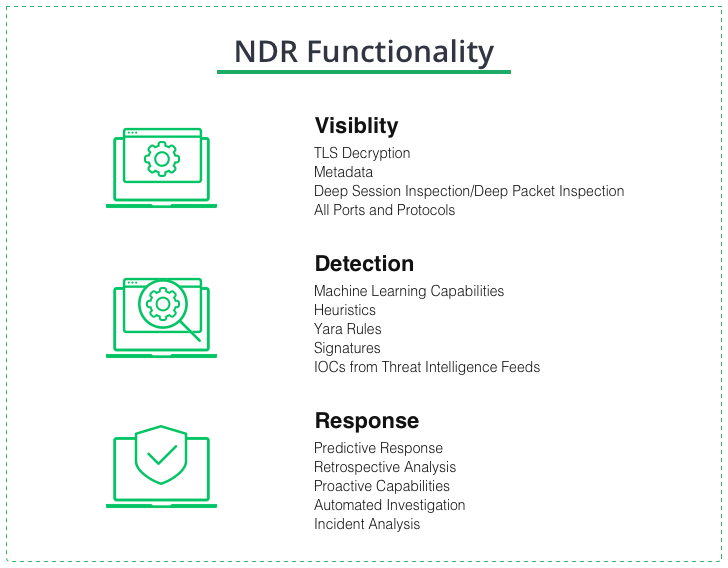
NDR is a cybersecurity solution that uses network traffic analysis to detect and respond to security incidents. It monitors network traffic in real time to identify suspicious behaviour, such as malware infections, data exfiltration, and unauthorised access attempts. NDR can also provide forensic analysis of network traffic to determine the root cause of an incident and help prevent future attacks.
The first NDR system (or NDR-like solutions) appeared in the early 2000s. The first commercial NDR solution was developed shortly after – in 2001 – by Arbor Networks. The software kit, called Peakflow, was designed to detect and mitigate DDoS attacks on networks. Since then, many other companies have developed their own NDR solutions, and the market for them has grown significantly as cyber threats have become more sophisticated. Some companies opt for developing their own, niche solutions of the same purpose, rather than use ones available on the market.
Why is NDR needed?
NDR is needed because traditional network security solutions, such as firewalls and antivirus software, are no longer sufficient to protect against threats that come from the network. Attackers can easily bypass these defences in a number of possible approaches. Most common ones are exploiting vulnerabilities, using social engineering, or advanced malware that is simply harder to detect. NDR provides an additional layer of defence by monitoring network traffic for suspicious behaviour that may indicate a security incident. Considering that over 60% of targeted cyberattacks on corporations happen with the use of an external network connection, mitigating that threat is a pretty demanded thing.
Threats NDR is Most Effective Against
Network detection and response solutions are not stand-alone, which means they can’t provide full-fledged protection without additional security utilities. Nonetheless, there are some areas where NDR is capable of being pretty close to self-sufficiency.
Insider threats are especially threatening to government organisations or other places that have to deal with classified documents. One cunning staff member may leak a lot of valuable, sometimes even vital data. NDR solutions can effectively detect insider threats, by monitoring network traffic for suspicious behaviour. It can successfully weed out unauthorised access attempts or unusual data transfers.
Advanced persistent threats (APT) rely heavily on the connection with its command and control centre. NDR solutions can detect APTs by analysing network traffic for unusual behaviour or communication with known APT infrastructure. Even while it cannot totally block the malware execution, it makes any attempts to communicate with it nearly impossible.
Distributed denial-of-service (DDoS) attacks are done from a slightly different angle. NDR solutions can detect and mitigate DDoS attacks by analysing network traffic for unusual traffic patterns or excessive traffic from known botnets. In situations when certain parts of the protected network are generating suspicious traffic, similar to one from a botnet, NDR will block it from accessing the Internet.
NDR, XDR, EDR – What is the Difference?
Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR) are also cybersecurity solutions that are designed to detect and respond to security incidents. However, they differ from NDR in several ways.
EDR focuses on monitoring endpoint devices, such as desktops, laptops, and servers, to detect and respond to security incidents. It was historically the first “advanced” security system that relies generally on behavioural analysis. XDR expands on EDR by integrating data from multiple sources, such as network traffic, cloud services, and endpoints. Such an all-encompassing control is needed to provide a more comprehensive view of the security posture of the protected environment.
In contrast, NDR focuses exclusively on network traffic analysis to detect and respond to security incidents. It provides visibility into network traffic that may not be visible to endpoint-based solutions and can detect threats that may not be visible on individual endpoints. Overall, both systems mentioned above may be effectively combined with network detection and response solutions. Such a symbiosis will improve the protection and provide security analysts with a more comprehensive set of data about the events.
Pros and Cons of Network Detection and Response
Ideals do not exist. Even the most advanced conceptions and solutions will still have certain problems that make it more difficult to implement and use. NDR is no exception.
Pros
- Provides real-time monitoring and detection of security incidents.
- Can detect threats that may not be visible on individual endpoints.
- Provides forensic analysis of network traffic to determine the root cause of an incident and help prevent future attacks.
- Provides visibility into network traffic that may not be visible to endpoint-based solutions.
- Can be integrated with other security solutions to provide a more comprehensive security posture.
Cons
- Requires significant expertise to set up and manage effectively.
- Can generate a large number of alerts that may be difficult to prioritise and investigate.
- Can be expensive to implement and maintain.
- Should be accompanied with specific hardware and software settings that allow it to do its job.
How does NDR differ from UBA and network sniffers?
User Behavior Analysis (UBA) is another cybersecurity solution that uses machine learning and artificial intelligence to detect suspicious behaviour. It looks for anomalies in user behaviour in order to uncover malicious activity, and network activity is among its sources of information. NDR solutions, on the other hand, concentrate their attention only on network activities. They also provide not just recommendations and alerts, as UBAs do, but a full-featured response to a detected threat.
Network sniffers are tools that capture and analyse network traffic for troubleshooting, optimization and investigation purposes. While network sniffers can detect suspicious traffic patterns, they are not designed to detect security incidents. They can still provide security teams with exhaustive information, sometimes even overwhelming what NDR provides. However, all the actions needed to mitigate the issue present in sniffer logs are about to be done manually.
Is NDR worth using?
NDR is a valuable cybersecurity solution for any organisation that has a network infrastructure. However, the cost and complexity of implementing and maintaining an NDR solution may make it less practical for small businesses. Needless to say that for home users NDRs are no-go, as it is simply excessive for the possible scale of network people can have at home.
Large companies with complex network infrastructures and a high risk of cyber threats may benefit the most from using NDR. The potential attack surface created by extensive LAN or WAN networks is hard to control manually. Even when a small fix is needed, its introduction to all the systems may take days to complete. Needless to say that more extensive and urgent changes may be a real problem. Network detection and response will not just protect, but help with automation of all these changes.