The National Security Agency (NSA) and several other cyber security partner agencies recently shared an advisory where they recommended to system administrators to use PowerShell in order to prevent and also detect all the malicious activities going on any Windows machine.
PowerShell (or shortly PS) is Microsoft’s automation and configuration tool. Hackers often abuse it, mostly at stages after gaining initial access to the system. But according to the advisory, defenders can actually have some benefits from the tool in terms of enhancing their incident responses, automating some repetitive tasks and helping with forensic efforts.
The NSA and cyber security centers in the U.S. (CISA), New Zealand (NZ NCSC), and the U.K. (NCSC-UK) issued a mutual advisory. It consists of several recommendations on how to use the tool in counteracting cyber threats successfully. These advices appear to be alternative to removing or disabling the tool.
“Blocking PowerShell hinders defensive capabilities that current versions of PowerShell can provide, and prevents components of the Windows operating system from running properly. Recent versions of PowerShell with improved capabilities and options can assist defenders in countering abuse of PowerShell” goes in an advisory.
PS can help to detect its malicious exploitation
Among the many advises the report gives one of them is to record PowerShell activity and also monitor the logs. The recommendation implies that such actions should help in the early detection of signs of potential abuse of PS.
Report also proposes to turn on features like Over-the-Shoulder transcription (OTS), Module Logging and Deep Script Block Logging (DSBL).
Deep Script Block Logging (DSBL) and Module Logging will build a complete database of logs. This database will be useful for detection of suspicious or malicious activity of PowerShell tools. The features will also include scripts that crooks use in the process and hidden actions/commands.
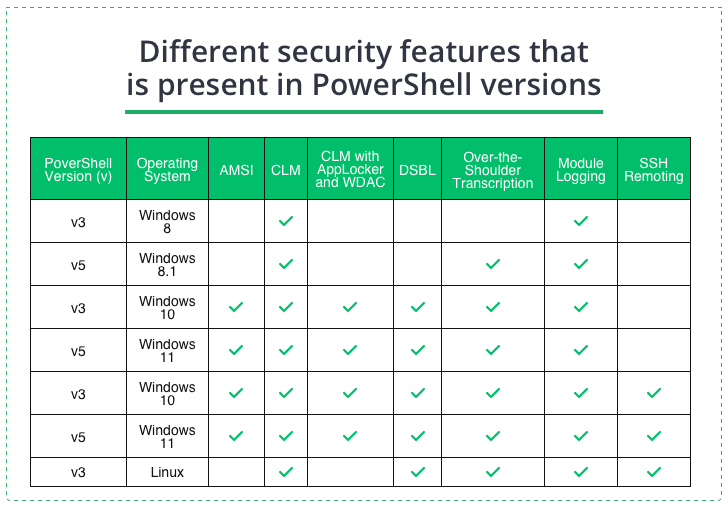
PowerShell security features in different Windows versions
OTS or Over-the-Shoulder transcription will help to record all PS input or output. This element can predict what threat actor’s next moves could be.
PowerShell can lower its own risk of abuse
Here it is noted that to reduce the risk of PowerShell abuse the tool needs to be leveraged in its capabilities and in such frameworks as PowerShell remoting. PS remoting won’t expose plain-text credentials when there would be commands that are executed remotely on Windows hosts.
One thing to add here is that administrators should also be aware that if this feature is enabled on some private network Windows Firewall automatically receives a rule that will permit all new connections.
But to customize Windows Firewall to allow connections only from trusted endpoints and networks will help to deter threat actor’s lateral movement across the network.
Concerning remote connections agencies recommend to use the Secure Shell protocol (SSH) which is supported in PowerShell 7.
One last main recommendation was also to use Windows Defender Application Control (WDAC) or AppLocker to set the tool into Constrained Language Mode (CLM) and so to deny all operations outside administrator’s policies.
“Proper configuration of WDAC or AppLocker on Windows 10+ helps to prevent a malicious actor from gaining full control over a PowerShell session and the host” also goes in the report.
To read the full advisory which is titled “Keeping PowerShell: Security Measures to Use and Embrace” you can here [PDF].