Both simple users, system administrators and virus analysts have the same opinion about ransomware. They usually consider it the most dangerous and unpredictable malware. It is hard to foresee its penetration, and literally impossible to deal with it without using special tools. However, the majority of ransomware units may be blocked with a good antivirus, giving it no chance to launch and make its dirty deed. So why is it still a menace and why do we have so many fears about it?
Ransomware dynamics
A lot of experienced users, as well as system administrators, have a bit obsolete information about ransomware. The sources where they found information about this type of malware state the next:
- Virus starts its attack instantly after being injected into the victim’s computer;
- Ransomware creators distribute only a little part of total circulation. The biggest share of malware spreading is after outsourcers, who were employed through the darknet channels:
- Attack has a chaotic character. There is no strict target, as well as no strategy of distribution/launching.
Such characteristics of ransomware were actual for the majority of families up to 2019. But the system where there are a lot of “external” people is prone to malfunctioning or even failure. Another disadvantage of such a scheme is that ransomware developers must pay the pre-approved percent of total income to their affiliates, decreasing their own profit. That’s why cybercriminals decided to go another way.
The attacks that are targeted on the specific company were spotted even in 2015, but they were not so massive. In 2017, we saw a WannaCry breakout1, when hundreds of corporations throughout the world were under attack, getting their data encrypted and OS blocked. But WannaCry was also used to infect the users with the mentioned model with the chaotic distribution. The separated ransomware families which were used to attack only the companies appeared only in early 2019.
Corporate attacks: what is common and different
The strategy used by the creators of such ransomware families is much more elaborated. They choose the target preciously, collecting the information about this corporation. Then, the ransomware injection happens, with the same methods as was in use earlier. However, after the successful injection, ransomware may stay inactive for a long time (as statistics show, about 56 days). What happens during this term?
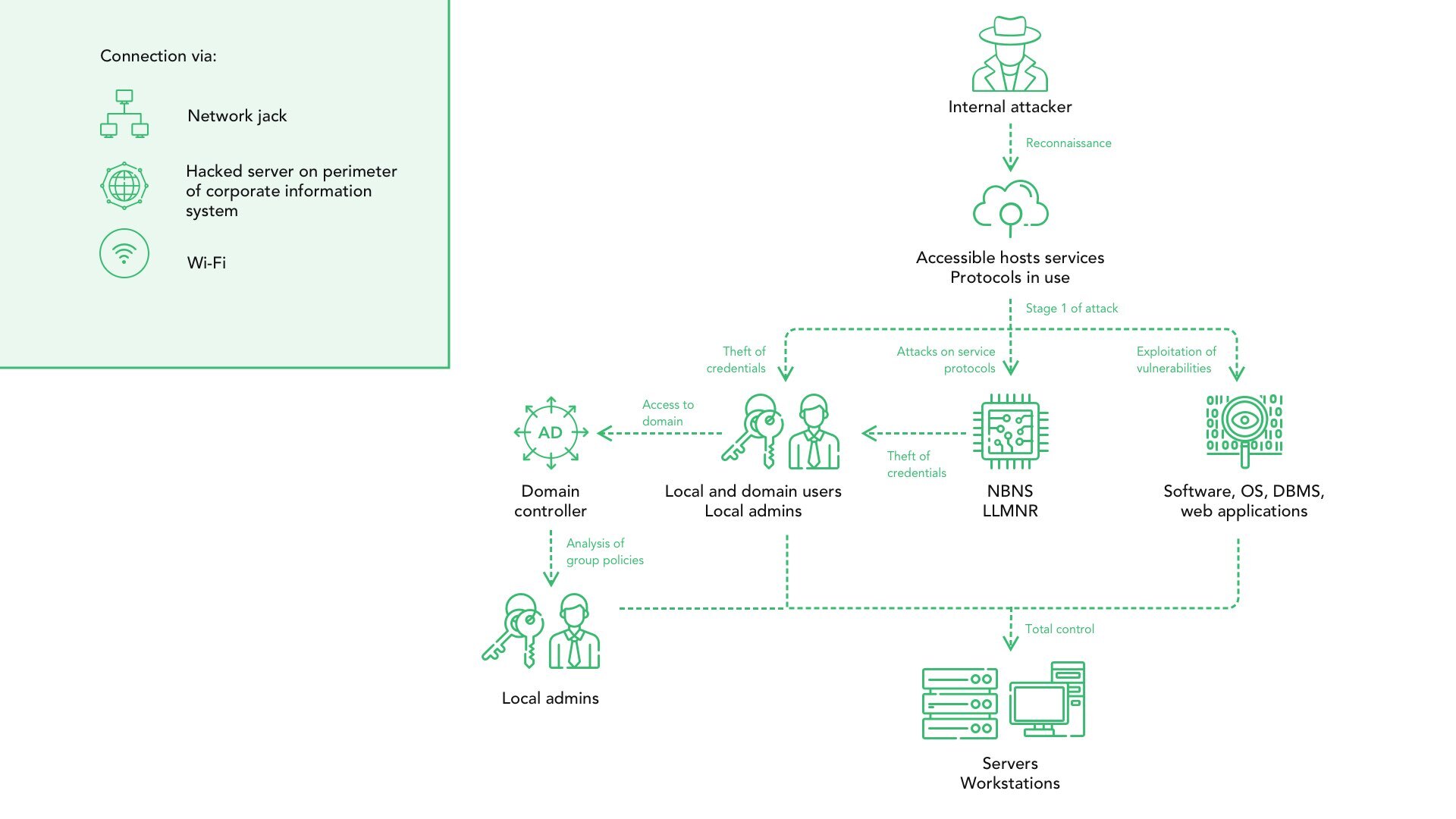
In the process of malware injection ransomware creators get access to the corporate network, using hack tools and searching for exploits with remote-access trojans (RAT). With these tools, they are able to figure out which computers store more important information, to choose the target more precious to deal more damage (and increase the chance of paying the ransom). Some of the important data may be stolen and then sold in the darknet, or the additional ransom can be asked to prevent sharing of this data.
Besides inspecting the network, malware operators usually inject the other viruses, which are called to block the anti-malware software. Such an action allows them to avoid detection while preparing the attack. Changing the system settings in order of antivirus blocking is not the only thing cybercriminals do with the systems: to prevent the backup usage for data recovery, they inspect the system to figure out which backup method is used. Then, crooks make the corresponding changes in the ransomware attack algorithm.
How ransomware reaches your company network
Before talking about the possible ways of network protection, let’s say several words about the ways of ransomware injection. They have not changed significantly: the largest share is still after email spamming; the second place is after the software cracking tools, like KMSPico or keygens of some sort. The third place (about 12% of total cases) is after the RDP vulnerabilities exploitation – quite an unusual method for other ransomware families.
Email spamming appears to be very effective because of the common reputation of email letters. One more letter with the consignment notes for the last production delivery, what can be wrong with it? Secretary, or whoever gets such a letter will open it without any suspicions. And the virus is right inside.
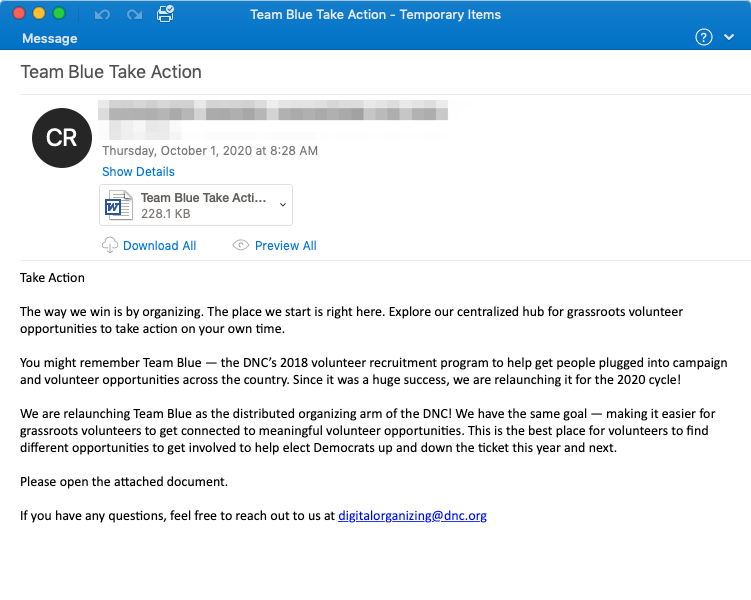
Classic email spam example. Malware is inside of the attached file.
A very little number of attacks are done without any interaction with the internal parts of the network. The only thing cybercriminals need to perform this attack is network vulnerability, which may easily be found by experienced users who have a sustainable knowledge in network security.
How to make your corporate network invulnerable to ransomware?
This question causes the massive disputes between experienced users. There are too many differences between the structure of different companies to make a single answer that will fit every network. Nonetheless, the kit of unwritten rules which must be followed while establishing the network for any company is below:
- Close all possible exploits. Remote desktop protocol, Microsoft Office macro, local user profiles, Windows Script host – all of them may be used by cybercriminals to inject the ransomware or to make the system less sustainable.
- Make the credentials isolated from people. Even the chiefs can make a mistake, telling someone a password or hiring the staff who can do so. The best solution is to cut all possible contacts of personnel with this data or to make credentials extremely long and complicated, so it will be too hard to remember it or write it down without mistakes.
- Minimize the possible damage of the attack. Network clusterization can help you to make the damage concentrated in a single part of the network, without dealing damage to other branches. Moreover, cybercriminals may cancel the attack when they see that the possibility of harming important computers goes to zero.
- Use anti-malware software. It may be very expensive to purchase the annual license for antivirus for every computer you have in your office. But all computers that contain the credentials or have a contact with them must be protected with an antivirus tool. I’d suggest you to use Loaris Trojan Remover – easy-to-use and effective tool.
 Is a real RED light for the different kinds of spyware
Is a real RED light for the different kinds of spyware
Once again – these advice are not ultimate and cannot guarantee that your network will be 100% safe, and you may forget about this problem. However, if you understand what to do to make your network protected, but don’t know which step will be better to begin from – take this list.