When it comes to cyber threat protection, most average users’ first thing to mind is an anti-virus. However, when protecting an entire organization, complex solutions, and entire solution systems come into play. One is User Behaviour Analytics, or UBA, which we will discuss in this article.
What is User Behavior Analytics?
User Behavior Analytics is a crucial aspect of cybersecurity that has gained immense popularity in recent years. UBA is a powerful tool that enables organizations to identify and mitigate cyber threats by analyzing user behavior patterns. This technology is instrumental in detecting insider threats that may go unnoticed by traditional security tools. Although the concept of UBA is not new, recent technological advancements have made it more effective and accessible than ever before. It leverages machine learning algorithms and statistical analysis to monitor and analyze user activity. This activity includes logins, file access, network traffic, etc. Then, the system compares this activity to baseline behavior patterns to identify anomalies and potential threats.
How does it work?
Since UBA relies on advanced machine learning algorithms and statistical models, it can more precisely identify abnormal user behavior. These models can identify unusual user behavior that deviates from established norms and detect suspicious activities often associated with cyber-attacks. In other words, UBA is designed to help identify cyber threats that would otherwise be difficult to see using traditional security tools such as firewalls and intrusion detection systems.
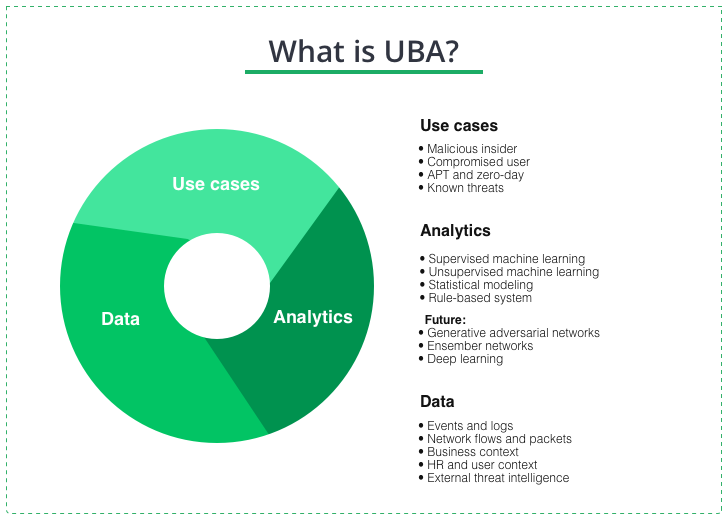
The main UBA functions
The primary use of UBA in security analytics is to predict a potential threat before it occurs and to support incident response for existing security threats. In this way, security professionals have found that, unlike using a generic approach, they can direct actionable insights into potential security threats by focusing on the predictive capabilities of UBA.
Using UBA technology as part of a company’s security involves collecting a vast amount of data supplied by SIEMs (Security information and event management) about how users behave on the company’s network or otherwise access company data. When this data is collected, the system analyzes it to determine what behavior is normal and what is not and sends an alert to the SIEM tool. Thus, the security team can quickly identify abnormal user behavior and continuously monitor such behavior as a potential security threat.
Why Companies Need UEBA
Today more and more businesses continue to digitize their operations. So, the use of UBA, along with other automated data analysis systems has become increasingly important. However, since most companies store critical data in their networks, they are a prime target for cybercriminals. Businesses are forced to adopt advanced security measures to protect their networks and confidential information.
Particularly, UBA is useful in detecting insider threats. Insiders typically have legitimate access to the network, and their activities are less likely to trigger traditional security tools. Nevertheless, UBA analyzes user activity logs and identifies patterns that suggest malicious behavior. For example, UBA can detect strange login attempts, unusual data access, and large amounts of data transfer to external devices. Logins from an unusual place, abnormal network activity and the like will trigger UBA attention as well.
SIEM, UBA, and SOAR
Despite nominally being a stand-alone cybersecurity product, UBA shows its advantages best when chained with other security tools. A wide range of narrowly-targeted anti-malware systems, event orchestration and response utilities can have pretty easy integration with each other. Having an additional source of information, such as User Behaviour Analytics system, is highly appreciated. This will boost not only overall visibility in the environment but also make security more reliable and ease incident forensics.
Most common systems UBA targets at integrating with are SIEM and SOAR (Security Orchestration and Response). The latter primarily aims at making a decision on the needed actions in the protected environment. Using a powerful data source, such as UBA/UEBA to “fuel” the SOAR significantly simplifies detecting abnormal behavior and preventing attacks. In addition, UBA can be used to configure the SIEM system, specifying the list of events that should be tracked and sent to the SOAR system for processing and decision-making.
UBA vs. UEBA
Although UBA is sometimes called user and entity behavior analytics or UEBA, the term UEBA has the letter E added, which stands for “entity.” So, the user is just one category of entities with observable behaviors on modern networks. In addition to human users, it analyzes nonhuman elements such as applications, IoT devices, and bots. Today, however, the two terms are often used interchangeably.
User Behavior Analytics is an essential tool in the fight against cyber threats. Its ability to detect insider threats and other sophisticated cyber-attacks makes it valuable to any organization’s security arsenal. While it may not replace traditional security tools, it can provide additional protection to help organizations avoid cyber threats. Moreover, with the increasing sophistication of cyber-attacks, UBA still plays a critical role in ensuring the security of networks and sensitive information.