When you log into your online accounts, there is a process called “authentication”. This is how you prove to the service that you are the person you’ve introduced as. Traditionally, people did this with a username and password. Unfortunately, this is not a very reliable way to do it today. Usernames are often easy to discover; sometimes, it’s your email address. Because passwords can be hard to remember, people usually choose simple ones or, even worse, use the same password on different sites.
That’s why almost all online services — banks, social networks, mailing clients — have added a way to increase the security of your accounts. Have you heard terms like “two-step verification” or “multi-factor authentication”? Both of these things are similar, and work on the same principle. When you first log into an account on a new device or in a new application, you need more than just a username and password – of course, if this function is set up. It would help if you had a second thing – what we call the second “factor”-to prove who you are.
How does an MFA work?
Suppose you log in to your work or study account and enter your username and password. If that’s all you need, anyone who knows your username and password can log in under your name. However, if you have multi-factor authentication enabled, things get more interesting. Every time you log in for the first time after entering your username and password, you’ll need to verify your identity with several available options on how to do it. For example, it could be a one-time password (OTP) via an authentication app or SMS or entering biometric information such as a fingerprint or facial scan.
That way, if someone else tries to log in as you, enter your username and password, and at the point where they are prompted for an additional factor, they are stuck! They won’t get past this step if they don’t have your smartphone or a physical token such as a reading card or key. Furthermore, these codes are usually dynamic and change every 30 seconds. So even if scammers recognize the code you used to log in yesterday, they still won’t be able to use it.
Three Main Types of MFA Methods
An authentication factor is one way of confirming your identity when logging in. For example, a password is one of the factors that you know. There are three most common types of authenticators:
Something you know
- A password
- A PIN or passphrase
- A set of secret questions and their corresponding answers that only you know
To use the knowledge factor for MFA, the end user must correctly enter information corresponding to the details previously stored in the online application.
Something You Have
Before smartphones, users carried tokens or smart cards that generated a one-time password or access code (OTP) to be entered into the online application. However, most users install an authenticator app on their smartphones to generate OTP security keys on their devices.
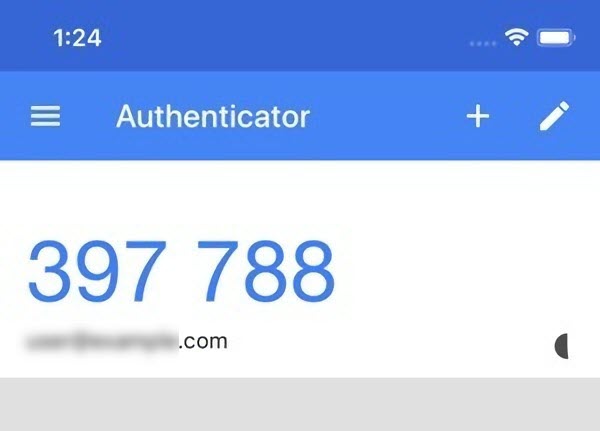
Google Authenticator is the most common means of additional authorization factor.
Something You Are
Biometric information about a person ranges from fingerprints, retinal scans, facial recognition, and voice recognition to behavior (such as how hard or fast a person types or swipes their finger across the screen).
To achieve multi-factor authentication, we must use at least two different technologies from at least two other technology groups for the authentication process. As a result, using a PIN in combination with a password will not be considered multi-factor authentication, while using a PIN with facial recognition as a second factor will. It is also acceptable to use more than two forms of authentication. However, most users increasingly require seamless authentication (verifying without performing validation).
Additional Forms of MFA
There are several other digital verification methods available to your customers:
Social Login
Social login is something that many users find convenient because they are usually already logged into their respective accounts. Remember that social media platforms are essential targets for hackers. Therefore, checking the social ID should not be the only method used besides the username/password in most cases.
Security Questions
Security questions are a kind of knowledge-based authentication in which the questions and answers are static. The business or the customer can define questions, and the customer provides solutions that are subsequently validated. Dynamic CRB, more secure than static, uses questions generated in real-time from data records such as credit history or transactions.
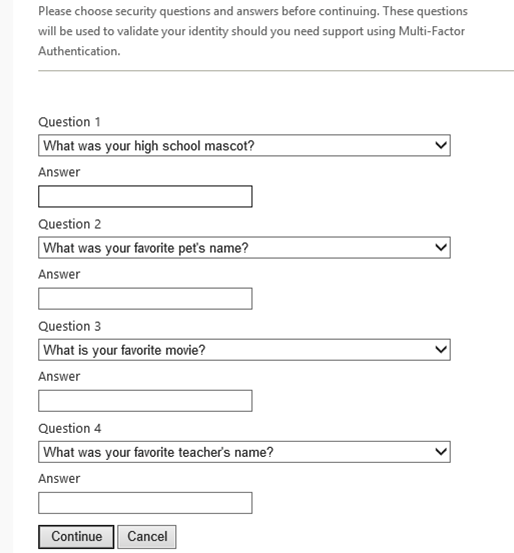
An example of questions that only the account owner knows the answers to.
Risk-Based Authentication
Security Systems can also use risk-based authentication with MFA. By tracking things like location, device, and even user keystrokes, you can tailor the frequency of MFA checks to the security situation. For example, RBA helps avoid repeated customer requests for additional verification when they log on from their “home” computer and location.
Time-based One-Time Passcode Authentication
TOTP is a password generated for a user at the current time and valid for a set time. Using this authentication method, you create a one-time password on the user side using a smartphone. Since TOTP has nothing to do with the server side, the user will always have access to their one-time password on their smartphone.
Multifactor authentication vs. two-factor authentication
When the first authentication methods were introduced, the goal was to provide security and make it as simple and convenient as possible. As a result, users were asked to give only two security keys to inform the system that these users passed the authentication. Typical forms of 2FA were user ID and password or ATM (ATM) bank card and PIN. Unfortunately, hackers quickly found ways to buy or crack passwords or withdraw money from ATM debit cards. This has prompted companies and security vendors to look for stricter forms of user authentication that use additional security factors for verification. The above methods of MFA are the results of the multi-year job for finding and mastering the more convenient application and usage.
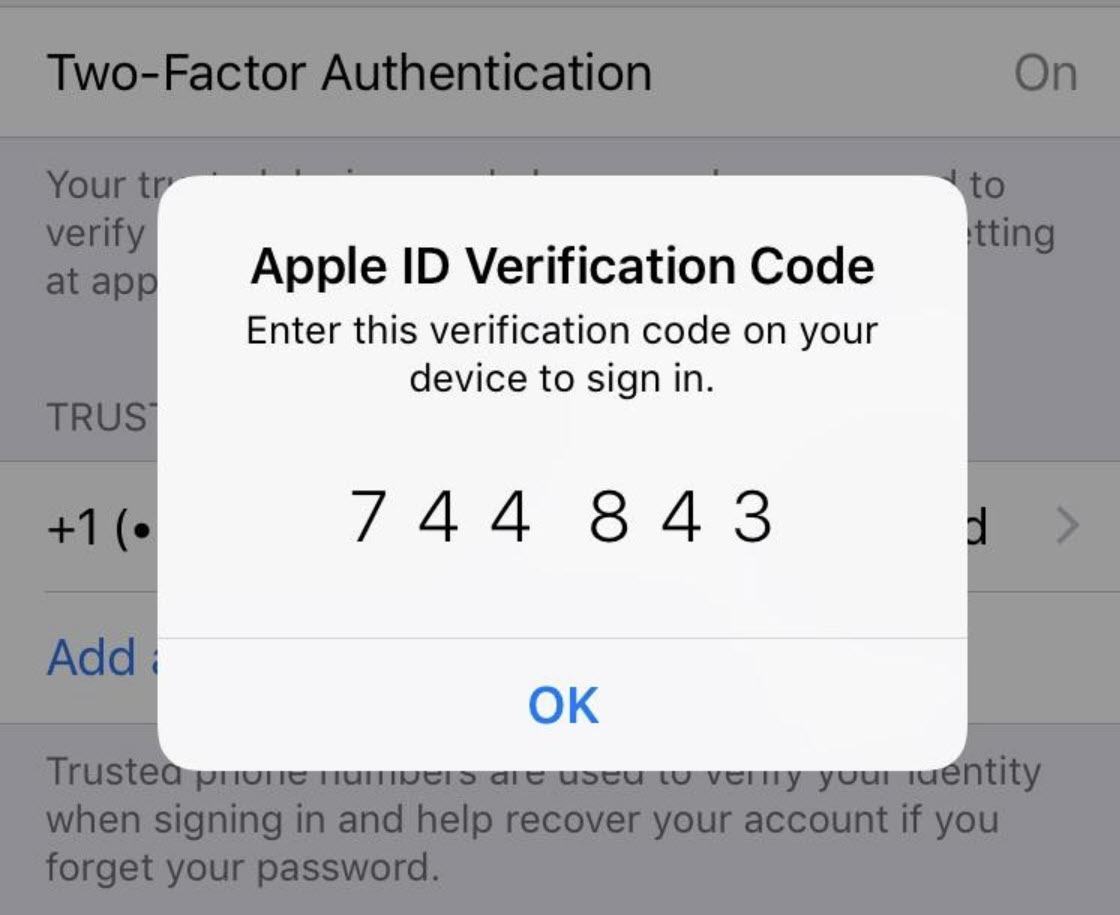
A classic example of two-factor authentication
The Benefits of MFA
The benefits of multi-factor authentication make up the experience that today’s consumers expect from any well-managed organization. MFA is quickly becoming the standard offering of the largest technology companies we can deal with today. Suppose you don’t meet these consumer expectations. In that case, you risk losing customers to companies that use MFA to protect their data from harm. Here’s what MFA gives you and your consumers:
- Improved security. Provides additional protection for consumers and employees on multiple layers of security.
- Increased customer trust. With additional security checks, consumers and employees can have confidence in the data.
- The main benefit of multi-factor authentication for businesses is the enhanced security protocols to protect the data.
- Multi-factor authentication enhances device security by requiring users (and potential hackers) to go through multiple identifiers. However, this makes it much more complex than using a single username and password combination for access.
- The chance that phishing attacks and data breaches will be successful drops dramatically when the second factor is introduced. This makes it more problematic for hackers to uninvite your company’s data.
- As long as the password is stored somewhere in an unencrypted form, it can be hacked. Many businesses have implemented multi-factor or two-factor authentication to reduce the risk of logging in with one username and password.
- This list, of course, is not exhaustive. There are also many secondary benefits, varying from industry to industry. For example, multi-factor authentication allows you to balance customer service with today’s security requirements. As a result, it’s not only one of the best ways to protect the login process but also to show customers that security is essential.
