Rootkit is a malicious program that threat actors use to gain unauthorized deep level access to the victim’s machine or it can also be a collection of malware tools both giving control over the machine.
In the past rootkits were used by computer and network administrators for various legitimate reasons like providing remote support to end users. But threat actors usually use malware as a backdoor to install other malicious programs like viruses, keyloggers or ransomware or as a way to help them further attack a compromised network.
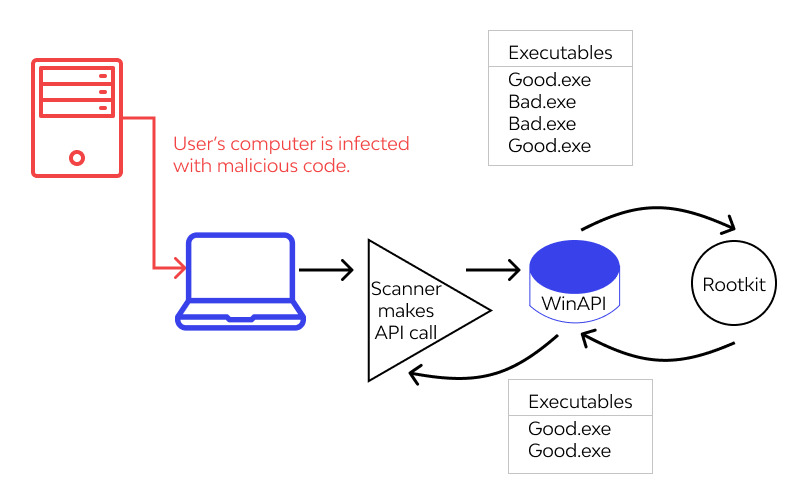
Visualization on how rootkit works
Rootkit is very stealthy malware; it can quite successfully make attempts to prevent its detection by disabling antivirus protection. But most today’s antivirus products detect them without an effort.
Cybercriminals often sell rootkits on the dark web for other criminals to use who then can use the malware in social engineering attacks or phishing attacks to lure victims into installing it.
How Does Rootkit Infect
Rootkit doesn’t spread by itself; targeted users should activate it. For example, a user gives permission for the rootkit installer program for its installation on their computer. The malware then installs and may lie dormant until the time will come.
The malware rootkit family includes keyloggers, password stealers, banking credential stealers, antivirus disablers and DoS bots.
Usual ways for the rootkits to spread are malicious Microsoft Word documents, PDF files, malicious executable files and phishing emails.
What Rootkit Can Do
Once on a system rootkit may do:
- Alter system configuration
Rootkit can create its own specific settings to the way hardware and software interact with each other on a targeted device. Not only they rootkit can also interfere with the work of the operating system controlling this component too. Malware decides which processes will run within a system, what software should be active and see what other devices are currently connected to main one; - Steal valuable information
One of the main tasks of rootkits is to steal sensitive and proprietary info. Bots, backdoors, adware, spyware, screen scrapers and keyloggers all do the malicious action; - Steal keystrokes
Payload rootkits steal information while the victim types anything on a keyboard. Everything that you, for example, typed in when doing online orders gets sent to threat actors. The other thing such rootkits can do is to send spam emails with other rootkits on board. Unknowingly, new victim will open such an email and instantly gets infected with rootkit; - Delete files
Contrary to the stealing files rootkits can also delete files. They get installed via backdoor on a network, device or system. Such example of an infection is possible when there’s found by threat actors vulnerability in OS or in general security of a device and often compromise happens during login; - Install malware
Rootkits can install other malware onto the victim’s device like adware, spyware, ransomware, trojans, worms, viruses, etc.
How Do I Know I Have Rootkit
Although it’s hard to detect rootkit as one of its main features is invisibility to targeted user but some common signs can hint that you may have this type of infection on board:
- Experiencing computer lockups
Your computer doesn’t respond to mouse or keyboard inputs. Or you can’t simply access your computer. This kind of thing may happen often and sometimes bring your computer to an extent that you can’t longer work with it; - You started to have certain performance issues
It may be that your browser started making strange redirects or you have noticed unusually high CPU usage. And, on the contrary, your computer began to perform very slow. - Your Windows settings has been changed
You also noticed that your Windows settings have been changed but without you actually remembering doing so. Your background images frequently change or disappear, some new pinned items appear in a taskbar. All this could possibly indicate rootkit infection; - Antivirus software doesn’t work
We mean here not that it doesn’t detect or remove malicious items but that it was disabled — again without your consent. Generally, not running antivirus software is one of the classic signs of infection because not only rootkits tend to disable this software first hand but other malware also have tendency to do this. - Companies should regularly monitor behavior of their workers
An example could be the next: some worker who normally accesses the system during daytime in New York suddenly turns up to access it at nighttime somewhere in South America. This fact could possibly be slightly suspicion sign of someone not from your company compromising your system before compromising the account of your worker; - Companies should also regularly monitor network activity
Company’s IT teams need to keep a constant watch over network activity and see whether anywhere the level of activity can be considered abnormal. Look if network nodes don’t go suddenly offline or level of network activity seems to be too high; - Regularly update software
Threat actors constantly look for vulnerabilities in OS and other software to exploit it not only with rootkits. Companies are aware of such things and also constantly trying to improve their products by issuing patches for any vulnerabilities found. Try to keep a regular update of your software and OS not leaving any chances for threat actors; - Have good and quality antivirus solution
These days any good and quality antivirus software can detect rootkits. We know it can be a more overwhelming task to find yourself an antivirus solution than dealing with rootkit itself but the efforts should be worth the try.
How Do I Prevent Rootkit Attack
To prevent infection with rootkit you can do by following simple tips on how to stay away from the threat: