Updating Windows is the process of fixing security vulnerabilities. However, resourceful cybercriminals have found a way to use this to spread malware. They don’t need to hack anything to do this. Instead, their task is to convince the victim that the fake Windows update is valid. This is how scammers distribute Aurora spyware, disguising it as a Windows update.
What are Fake Windows Update?
Fake Windows updates are a common tactic for spreading malicious software. It is designed to trick users into downloading and installing malware onto their computers. These fake updates may appear convincing, using logos, design elements, and language similar to genuine Windows updates. Thus, it makes it difficult for some users to differentiate between the real and fake. However, they have one feature that distinguishes them from the actual updates.
True Windows Update
You need to understand what valid updates are to distinguish between fake and valid ones. Starting with Windows 10, updates for all Windows components are in one place – Settings – Windows Updates. This is the only place where any updates occur, whether system updates, driver updates, or Microsoft Defender updates. Sometimes an icon may appear in the lower right corner or tray; this is normal. Although Windows 11 removed such a pushy update mode, Windows 10 could suddenly start updating at any inopportune moment. That could be what put users’ vigilance to sleep and made Aurora’s distribution methods effective.
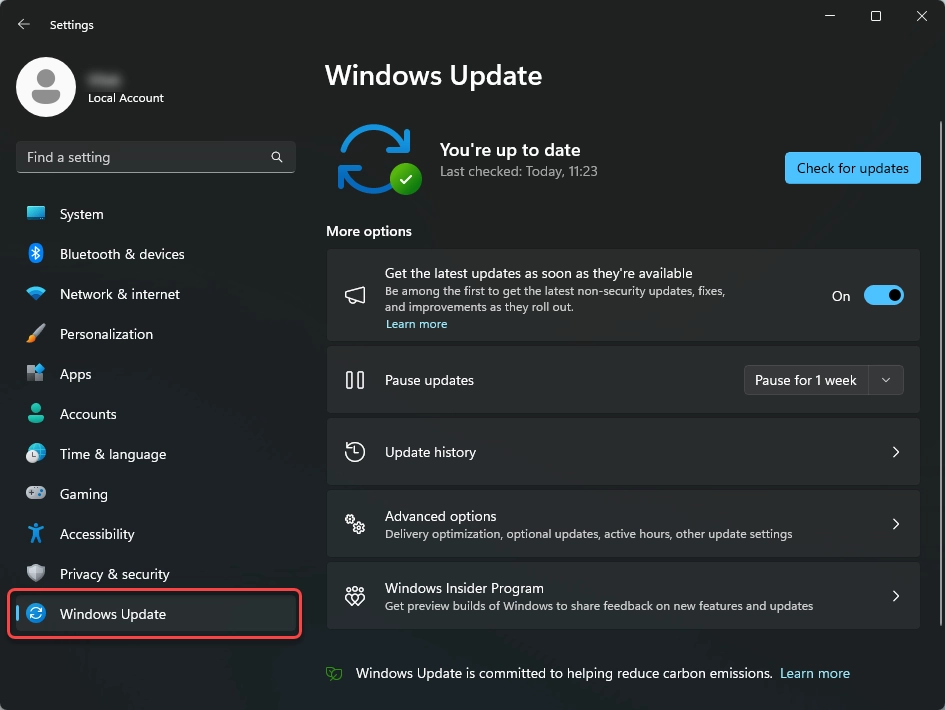
Signs of Fake Windows Update
Unlike the above signs of legitimate Windows updates, fake ones may take the form of system notifications, browser notifications or display an animation that looks like a natural update process. Usually, this is a Windows update animation, which suddenly stops at 95% and shows a message to the user that they need to update their browser. Despite a certain absurdity for confident PC users, newcomers may download and run the installation file ChromeUpdate.exe. However, instead of an updated browser, the victim receives malware.
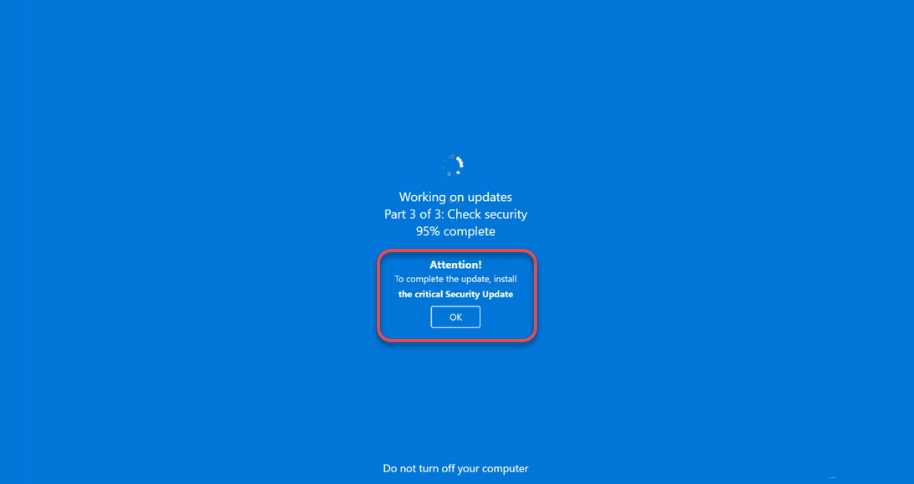
Fake Windows update window. Original updates don’t ask you to install anything else.
What is an Aurora Stealer?
Aurora is a relatively new info stealer that appeared in the fall of 2022. It is an average information-stealing malware that steals browser data, session tokens, cryptocurrencies, and a small piece of system information. This information is needed to create a system fingerprint. It includes the system name, user name, HWID, CPU, RAM, GPU, screen resolution, and location of the malware file.
Next, the malware checks the web browsing files to find login information. It then looks for cryptocurrency wallet extensions and checks the AppData/Roaming folder for cryptocurrency desktop applications. Lastly, Aurora tries to steal credentials for several popular apps, such as Discord or Steam.
Like most of the nefariousness, Aurora is related to Russia. This is evidenced by the pool of URLs used to display banners. Moreover, some of them contain obscene language in Russian:
- chistauyavoda[.]ru
- activessd6[.]ru
- pochelvpizdy[.]ru
- activessd[.]ru
- grhfgetraeg6yrt[.]site
- oled8kultra[.]ru
- evatds[.]ru
- clickaineasdfer[.]ru
- activedebian[.]ru
- click7adilla[.]ru
- shluhapizdec[.]ru
- 04042023[.]ru
- oled8kultra[.]site
- activehdd[.]ru
- moskovpizda[.]ru
- xhamster-18[.]ru
- xxxxxxxxxxxxxx[.]ru
Many of these websites pretended to be adult websites imitating a fake Windows update. However, some could not be accessed because they did not respond. This is probably because the virus changes the system’s network settings, forcing it to connect to a specific site through a particular port.
Additionally, researchers found that some of the websites owned by this attacker were not downloading malware. Instead, they were posting YouTube videos that promoted Russia. As pointless an action as most others of this country but not so damaging. However, much more interesting is the method of spreading this malware.
How to remove Aurora Stealer?
The best defense against adware infection is vigilance when surfing the Web. As mentioned, such tricks are designed for the human factor, so attentiveness and cyber hygiene will minimize accidental malware infections. However, there are some more specific tips:
- Avoid questionable sources of software downloads. These are usually pirate sites that are usually unmoderated and torrent trackers where no one checks the content.
- Do not use hacked software. Licensed software can be costly, encouraging freeloaders to download paid software with removed license checks or patches (cracks) that do it on the spot. Since this is an illegal action (which is obvious), the author asks to disable anti-virus software in the description of such programs. However, the person who hacked the program often wants to eat, too, so he may inject a bonus as a Trojan into his child.
- Use protection solutions. Malware or adware can penetrate deep into your system and can be pretty difficult to find and remove. If you are a victim of adware, you need a powerful tool that can scan your system and find and remove the entire infection from your device.
